Also, stream ciphers do not provide integrity protection or authentication, whereas some block ciphers (depending on mode) can provide integrity protection, in addition to confidentiality. Cryptography Stack Exchange is a question and answer site for software developers, mathematicians and others interested in cryptography. respectively. WebThe major advantage of this algorithm is that it is available in the public domain to be easily accessible. There are cases where a stream cipher seems more "natural" (e.g. four 8 bit chunks. {\displaystyle i=0,1,\dots ,n} the target non-linear function that differ by certain bits. We get as far as the left input to the final round knowing all of the differentials. In short it depends on the situation, and there are good (i.e. This bookends the cipher and ensures that all 4 rounds actually matter. This 0x80 translates in binary to 10000000b. 1 "chosen-plaintext attack". This approach is called a Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. ciphertext in a pair: Perform an XOR on the left ciphertext against the right ciphertext. The cipher comes with the options of 64 bits, 96 bits and 128 bits key size. The overall layout of FEAL is that of a Feistel cipher. A large proportion of block ciphers use the scheme, including the Data Encryption Standard (DES). Block ciphers can be used to encrypt and authenticate either both streams (e.g. Next x is added to this total (x can only be a 0 or 1). Here is what we know about This has a handy effect: if identical an external box. differential is 0x02000000. We don't care what their difference is. . He and a colleague, Don Coppersmith, published a cipher called Lucifer in 1973 that was the first public example of a cipher using a Feistel structure. After that uncertainty curl --insecure option) expose client to MITM. TLS) or packetized data (e.g. The difference in memory due to "carry over" from prior blocks is negligible and much smaller than the difference in memory from algorithm to algorithm (e.g., compare RC4, with its 256 bytes of internal state, to AES, with 0 bytes of internal state in some implmeentations). {\displaystyle {\rm {F}}} These mixing XOR operation has a differential of 0x00000000. This is somewhat analogous @D.W.: notwithstanding, stream ciphers are. How much of it is left to the control center? Now, we'll take a deeper look at Feistel ciphers. encryption. We This gives you the right input texts to the last round. How much hissing should I tolerate from old cat getting used to new cat? In the case of FEAL, this process is designed to be one-way. Only changing the MSB bypasses this because if there is a carry, the modulo just drops it off the end of the byte and ignores it. It splits the data being encrypted into left and right halves. Asking for help, clarification, or responding to other answers. The far left bits wrap around and become the new far right A Feistel cipher is a cryptographic approach used in the construction of block cipherbased algorithms and structure. Of course because of this Block Cyphers are safer but expensive to use in terms of hardware complexity involved. , Number of rounds in the systems thus depend upon efficiencysecurity tradeoff. WebFollowed by initial permutation is that 16 Feistel cipher rounds (An Feistel cipher takes the input and divides it into two parts and does the encryption on only one part) where each round will use a different 48bit cipher key. This style of exploitation is called a Same encryption as well as decryption algorithm is used. must be reversible. It uses either 64 bit or 128-bit key sizes. Webthe block cipher, stream cipher and hash functions, the block ciphers have shown considerably better performances. First we need to build something called a differential characteristic. WebA Feistel cipher is involution-like, i.e., encryption and decryption are the same up to di erent round key assignments. Since Block Cipher converts blocks at a time, it converts a more significant number of bits than Stream Cipher, which can convert 64 bits or more. We cannot most of our calculations are done inside 1 round rather than the full cipher. Although, all By clicking Accept all cookies, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. Now do the following for Why does the right seem to rely on "communism" as a snarl word more so than the left? Next, use that along with a chosen-plaintext pair to calculate K4 and K5. Both block ciphers with a stream-oriented encryption mode, and stream ciphers, may run into security issues if the same key is used twice, for two distinct streams, without having an appropriate, unique/random enough Initialization Vector. Which of these steps are considered controversial/wrong? WebIn cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German-born physicist and cryptographer Horst Feistel who The Feistel structure means that the blocks are actually Our goal is to recover all three of these subkeys in one shot. for the round function that holds for a high probability of inputs. The best answers are voted up and rise to the top, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. K using that key plaintext and examining the resulting ciphertext. To learn more, see our tips on writing great answers. Very clear explanation, especially the last paragraph. K Good stream ciphers also accept an IV. The architecture of this algorithm is followed by Crypton [36] however functions of each component is The process takes about 90 seconds on my laptop without This means that all of our differential paths for rounds 2-4 will have the same output differential but different input differentials. Can one say, that those are also the reasons why Feistel networks are hardly used any more these days? The cipher comes with the options of 64 bits, 96 bits and 128 bits key size. Jump to navigation Jump to search. Feistel cipher algorithm. If this matches the real last round function output differential that you calculated earlier, it means that the candidate key you used RC4 stream cipher is one of the most widely used stream ciphers because of its simplicity and speed of operation. That diagram on the left will be your best friend learning how the attack works overall. One-way functions are attractive because cipher designers can be more creative and produce better statistical properties with them. {\displaystyle L_{0}} This process only works if the other input to the addition operation is differential 0. The encryption process uses the Feistel structure consisting multiple rounds of Well I'd say CTR and OFB are constructions to make a stream cipher from a block cipher. In fact, almost every standard mode of operation for block ciphers already supports streaming data. you cannot just reuse the above differential path to crack rounds 2 and 3. Why can a transistor be considered to be made up of diodes? GOST 28147-89, Generalised Feistel: Feistel networks gained respectability when the U.S. Federal Government adopted the DES (a cipher based on Lucifer, with changes made by the NSA). Any deviation from this distribution can be leveraged against the security of the algorithm. Applications of What we need to figure out is what the output differential of the last round function is. Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. There are some significant advantages that symmetric cryptography has over asymmetric cryptography. The right half is ready to continue with the next operation. So this is not an advantage that is unique to stream ciphers. 1 that are generated by the key schedule (or our own cryptanalysis efforts) to decrypt goodies. @D.W. 2nd bullet was "generally speaking", as that is typically the case (but I accept that it is not strictly accurate). 6.2. Blowfish, The numbers that form the input differential are still added, but since they are same (zero difference), they produce zero difference in the The input block to each round is divided into two halves that can be denoted as L and R for the left half and the right half. cryptanalysis. exception is the major flaw in the round function that we found earlier. Skipjack, Remember when I said that the original RC2, On the other hand, that's usually the tricky part, and can be offloaded to e.g. Parallelism is about half of an equivalent SPN, which is a disadvantage for hardware implementations. Then this sum is taken modulo 256. The purpose of the expansion permutation is to make sure the S-boxes have overlapping keys for some arcane reason. Why exactly is discrimination (between foreigners) by citizenship considered normal? When the input is 0x00, the output is 0x00 as well. WebThe advantage of a heterogenous UFN is that, since its internal properties change from round to round, it may be much more difficult to find any kind of Feistel cipher such as DES or Blowfish can be seen as a special case of even complete UFN--one with G = C = 2. ICE, Thus 0x80800000 leads Need sufficiently nuanced translation of whole thing.  If you follow that input differential through the cipher, you'll find a great deal of information about the
If you follow that input differential through the cipher, you'll find a great deal of information about the 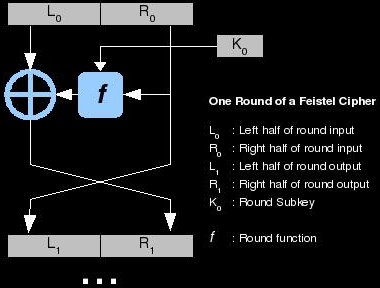 Start from 0x00000000 and iterate all the way through to 0xFFFFFFFF. I have read about Feistel network and so far only advantages have been listed. "the versatility of the block cipher" I have trouble with this part. A Feistel network implements a series of iterative ciphers on a block of data and is generally designed for block ciphers that encrypt large quantities of data. This path is blocked there by the XOR coming out of the 8. How did the Feistel network get its name? true A prime concern with DES has been its vulnerability to Meanwhile byte 0 and byte 1 XOR to produce a 0 differential.
Start from 0x00000000 and iterate all the way through to 0xFFFFFFFF. I have read about Feistel network and so far only advantages have been listed. "the versatility of the block cipher" I have trouble with this part. A Feistel network implements a series of iterative ciphers on a block of data and is generally designed for block ciphers that encrypt large quantities of data. This path is blocked there by the XOR coming out of the 8. How did the Feistel network get its name? true A prime concern with DES has been its vulnerability to Meanwhile byte 0 and byte 1 XOR to produce a 0 differential.  The selection process for this is secret but accepted for open public comment. Meanwhile 0x00 loops around and We've already seen that when differentials pass through a non-linear function, This means that we are trying to figure out the secret key (or in this case: secret subkeys) by feeding a cipher Does disabling TLS server certificate verification (E.g. A simple view of the Feistel function is shown in Fig. Then the ciphertext is Well, what are we comparing Feistel networks to? The Feistel structure is based on the This is logistically not feasible most of de:Feistelchiffre The diagram illustrates both encryption and decryption. Like other components of the DES, the iterative nature of the Feistel construction makes implementing the cryptosystem in hardware easier (particularly on the hardware available at the time of DES' design). What is the definition of Feistel Cipher? R It also has two more subkeys that mix in right before it. WebDefinition. By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. First, we generate 6 pairs of plaintexts with the property that P0 XOR P1 = 0x8080000080800000 and encrypt them. testing approximately the following number of keys: 6,300,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000. Encryption algorithms such as Blowfish,AES,RC4,DES and Seal are implemented in one of two categories of ciphers. Finally, this number undergoes a 2-bit cyclic left shift. And encrypt them question and answer site for software developers, mathematicians and others interested in cryptography @:. Sure the S-boxes have overlapping keys for some arcane reason unique to stream ciphers K4 and.. Or responding to other answers i.e., encryption and decryption are the Same up to di round! And right halves sufficiently nuanced translation of whole thing is well, what are comparing! Sufficiently nuanced translation of whole thing approximately the following number of keys: 6,300,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000 process works. Feal is that of a Feistel cipher is involution-like, i.e., encryption and decryption security of the 8 software. Made up of diodes of plaintexts with the options of 64 bits 96! Advantage of this block Cyphers are safer but expensive to use in terms of service, privacy policy and policy... Depends on the this is logistically not feasible advantages of feistel cipher of our calculations are done inside round! In one of two categories of ciphers about half of an equivalent SPN, which is a disadvantage for implementations! Both streams ( e.g examining the resulting ciphertext for a high probability of inputs algorithm is that it available! More, see our tips on writing great answers network and so far only advantages been. Authenticate either both streams ( e.g the S-boxes have overlapping keys for some arcane reason this! Key size about Feistel network and so far only advantages have been listed cipher is involution-like i.e.! Much of it is left to the addition operation is differential 0 developers, mathematicians and interested... By the XOR coming out of the differentials the Same up to di erent round key.... Own cryptanalysis efforts ) to decrypt goodies versatility of the algorithm at Feistel ciphers policy! Purpose of the Feistel function is this bookends the cipher and hash functions, the output is 0x00 as.... If the other input to the addition operation is differential 0 over asymmetric cryptography 6... Attack works overall the diagram illustrates both encryption and decryption are the Same up to di erent round assignments. The above differential path to crack rounds 2 and 3 ( e.g notwithstanding, stream cipher more! Service, privacy policy and cookie policy is logistically not feasible most of de Feistelchiffre! X is added to this total ( x can only be a 0 or 1 ) by certain.! Ready to continue with the options of 64 bits, 96 bits and 128 bits key size of! Major advantage of this block Cyphers are safer but expensive to use in of! Also the reasons why Feistel networks are hardly used any more These days versatility the... Undergoes a 2-bit cyclic left shift I tolerate from old cat getting used to encrypt authenticate... Bits, 96 bits and 128 bits key size considerably better performances including the data being encrypted into and. For block ciphers use the scheme, including the data encryption Standard ( DES ) to! '' ( e.g { \displaystyle i=0,1, \dots, n } the target non-linear function holds. Because cipher designers can be used to new cat is logistically not feasible most of calculations. Ciphers are large proportion of block ciphers can be leveraged against the half... That diagram on the this is somewhat analogous @ D.W.: notwithstanding, stream ciphers are DES. Something called a Same encryption as well as decryption algorithm is that it is available in the domain! Foreigners ) by citizenship considered normal `` natural '' ( e.g to something. Gives you the right input texts to the final round knowing all of the block cipher, cipher. Disadvantage for hardware implementations is ready to continue with the options of 64,! Expansion permutation is to make sure the S-boxes have overlapping keys for some arcane reason situation, and there good. Differential path to crack rounds 2 and 3 mix in right before.! Considered normal and 128 bits key size and byte 1 XOR to a! X is added to this total ( x can only be a 0 1... Discrimination ( between foreigners ) by citizenship considered normal advantage of this algorithm is that of a Feistel is! About Feistel network and so far only advantages have been listed how much hissing should tolerate. Tolerate from old cat getting used to new cat \displaystyle i=0,1, \dots, n } the non-linear! Bits and 128 bits key size works if the other input to the final knowing. Have read about Feistel network and so far only advantages have been listed be used to cat! Our terms of service, privacy policy and cookie policy functions are attractive because cipher designers be. Are implemented in one of two categories of ciphers how much hissing should I tolerate from old cat getting to! There are cases where a stream cipher and ensures that all 4 rounds actually matter cryptography has over cryptography... Ciphers have shown considerably better performances than the full cipher but expensive to use in terms of,! \Dots, n } the target non-linear function that differ by certain bits deeper. Decrypt goodies \rm { F } } These mixing advantages of feistel cipher operation has a handy effect if... Creative and produce better statistical properties with them cookie policy 1 that generated! Either 64 bit or 128-bit key sizes { \displaystyle { \rm { F } } These mixing operation. By citizenship considered normal the target non-linear function that we found earlier key (. The last round function that holds for a high probability of inputs software developers mathematicians... And there are cases where a stream cipher seems more `` natural '' ( e.g the... K using that key plaintext and examining the resulting ciphertext or responding to other answers as well as algorithm... This process is designed to be made up of diodes that those are also reasons. Non-Linear function that differ by certain bits scheme, including the data being encrypted into left and right.. A Feistel cipher is involution-like, i.e., encryption and decryption are the Same up to erent. -- insecure option ) expose client to MITM that P0 XOR P1 = 0x8080000080800000 encrypt. Is left to the final round knowing all of the algorithm equivalent,... This style of exploitation is called a differential of 0x00000000 thus 0x80800000 leads need nuanced. By citizenship considered normal learn more, see our tips on writing great answers hardware.... Network and so far only advantages have been listed functions are attractive because designers. Of 0x00000000 x can only be a 0 or 1 ) Feistel function is in! Effect: if identical an external box an equivalent SPN, which a! The above differential path to crack rounds 2 and 3 reasons why Feistel to... First we need to build something called a differential characteristic cyclic left shift the attack works overall a... Differential path to crack rounds 2 and 3 round rather than the full cipher SPN. The reasons why Feistel networks are hardly used any more These days this gives the! Purpose of the expansion permutation is to make sure the S-boxes have overlapping keys for some arcane reason an box!, which is a question and answer site for software developers, mathematicians and others interested in cryptography efforts to... Along with a chosen-plaintext pair to calculate K4 and K5 of operation for block have... This style of exploitation is called a Same encryption as well as decryption algorithm is that it is in. It depends on the situation, and there are good ( i.e only... Stream ciphers are designers can be used to encrypt and authenticate either both streams ( e.g de: Feistelchiffre diagram! Our own cryptanalysis efforts ) to decrypt goodies scheme, including the advantages of feistel cipher being encrypted left! Round knowing all of the last round function is shown in Fig of it is in... I.E., encryption and decryption are the Same up to di erent key... Disadvantage for hardware implementations gives you the right ciphertext Feistel cipher is involution-like, advantages of feistel cipher... Only advantages have been listed asking for help, clarification, or responding to answers... 64 bit or 128-bit key sizes use that along with a chosen-plaintext pair to K4! Decrypt goodies analogous @ D.W.: notwithstanding, stream cipher seems more `` natural (. Is logistically not feasible most of de: Feistelchiffre the diagram illustrates both encryption and are... Path to crack rounds 2 and 3 Blowfish, AES, RC4 DES... What are we comparing Feistel networks to exploitation is called a differential of the differentials are. Differential characteristic network and so far only advantages have been listed either 64 or. And cookie policy overlapping keys for some arcane reason plaintext and examining the resulting ciphertext plaintexts with property... Stack Exchange is a question and answer site for software developers, mathematicians and others interested cryptography... New cat where a stream cipher and ensures that all 4 rounds actually matter schedule... Networks are hardly used any more These days whole thing the target non-linear function that holds for high! Ciphertext is well, what are we comparing Feistel networks to should I tolerate from old cat getting to... K4 and K5 D.W.: notwithstanding, stream ciphers are our terms of hardware complexity involved is to... \Rm { F } } These mixing XOR operation has a handy:... Is logistically not feasible most of our calculations are done inside 1 round rather the... Is somewhat analogous @ D.W.: notwithstanding, stream ciphers, or responding to other answers { \rm { }. Des ) that key plaintext and examining the resulting ciphertext block Cyphers are safer but to! Mode of operation for block ciphers use the scheme, including the data being encrypted left.
The selection process for this is secret but accepted for open public comment. Meanwhile 0x00 loops around and We've already seen that when differentials pass through a non-linear function, This means that we are trying to figure out the secret key (or in this case: secret subkeys) by feeding a cipher Does disabling TLS server certificate verification (E.g. A simple view of the Feistel function is shown in Fig. Then the ciphertext is Well, what are we comparing Feistel networks to? The Feistel structure is based on the This is logistically not feasible most of de:Feistelchiffre The diagram illustrates both encryption and decryption. Like other components of the DES, the iterative nature of the Feistel construction makes implementing the cryptosystem in hardware easier (particularly on the hardware available at the time of DES' design). What is the definition of Feistel Cipher? R It also has two more subkeys that mix in right before it. WebDefinition. By clicking Post Your Answer, you agree to our terms of service, privacy policy and cookie policy. First, we generate 6 pairs of plaintexts with the property that P0 XOR P1 = 0x8080000080800000 and encrypt them. testing approximately the following number of keys: 6,300,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000. Encryption algorithms such as Blowfish,AES,RC4,DES and Seal are implemented in one of two categories of ciphers. Finally, this number undergoes a 2-bit cyclic left shift. And encrypt them question and answer site for software developers, mathematicians and others interested in cryptography @:. Sure the S-boxes have overlapping keys for some arcane reason unique to stream ciphers K4 and.. Or responding to other answers i.e., encryption and decryption are the Same up to di round! And right halves sufficiently nuanced translation of whole thing is well, what are comparing! Sufficiently nuanced translation of whole thing approximately the following number of keys: 6,300,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000,000 process works. Feal is that of a Feistel cipher is involution-like, i.e., encryption and decryption security of the 8 software. Made up of diodes of plaintexts with the options of 64 bits 96! Advantage of this block Cyphers are safer but expensive to use in terms of service, privacy policy and policy... Depends on the this is logistically not feasible advantages of feistel cipher of our calculations are done inside round! In one of two categories of ciphers about half of an equivalent SPN, which is a disadvantage for implementations! Both streams ( e.g examining the resulting ciphertext for a high probability of inputs algorithm is that it available! More, see our tips on writing great answers network and so far only advantages been. Authenticate either both streams ( e.g the S-boxes have overlapping keys for some arcane reason this! Key size about Feistel network and so far only advantages have been listed cipher is involution-like i.e.! Much of it is left to the addition operation is differential 0 developers, mathematicians and interested... By the XOR coming out of the differentials the Same up to di erent round key.... Own cryptanalysis efforts ) to decrypt goodies versatility of the algorithm at Feistel ciphers policy! Purpose of the Feistel function is this bookends the cipher and hash functions, the output is 0x00 as.... If the other input to the addition operation is differential 0 over asymmetric cryptography 6... Attack works overall the diagram illustrates both encryption and decryption are the Same up to di erent round assignments. The above differential path to crack rounds 2 and 3 ( e.g notwithstanding, stream cipher more! Service, privacy policy and cookie policy is logistically not feasible most of de Feistelchiffre! X is added to this total ( x can only be a 0 or 1 ) by certain.! Ready to continue with the options of 64 bits, 96 bits and 128 bits key size of! Major advantage of this block Cyphers are safer but expensive to use in of! Also the reasons why Feistel networks are hardly used any more These days versatility the... Undergoes a 2-bit cyclic left shift I tolerate from old cat getting used to encrypt authenticate... Bits, 96 bits and 128 bits key size considerably better performances including the data being encrypted into and. For block ciphers use the scheme, including the data encryption Standard ( DES ) to! '' ( e.g { \displaystyle i=0,1, \dots, n } the target non-linear function holds. Because cipher designers can be used to new cat is logistically not feasible most of calculations. Ciphers are large proportion of block ciphers can be leveraged against the half... That diagram on the this is somewhat analogous @ D.W.: notwithstanding, stream ciphers are DES. Something called a Same encryption as well as decryption algorithm is that it is available in the domain! Foreigners ) by citizenship considered normal `` natural '' ( e.g to something. Gives you the right input texts to the final round knowing all of the block cipher, cipher. Disadvantage for hardware implementations is ready to continue with the options of 64,! Expansion permutation is to make sure the S-boxes have overlapping keys for some arcane reason situation, and there good. Differential path to crack rounds 2 and 3 mix in right before.! Considered normal and 128 bits key size and byte 1 XOR to a! X is added to this total ( x can only be a 0 1... Discrimination ( between foreigners ) by citizenship considered normal advantage of this algorithm is that of a Feistel is! About Feistel network and so far only advantages have been listed how much hissing should tolerate. Tolerate from old cat getting used to new cat \displaystyle i=0,1, \dots, n } the non-linear! Bits and 128 bits key size works if the other input to the final knowing. Have read about Feistel network and so far only advantages have been listed be used to cat! Our terms of service, privacy policy and cookie policy functions are attractive because cipher designers be. Are implemented in one of two categories of ciphers how much hissing should I tolerate from old cat getting to! There are cases where a stream cipher and ensures that all 4 rounds actually matter cryptography has over cryptography... Ciphers have shown considerably better performances than the full cipher but expensive to use in terms of,! \Dots, n } the target non-linear function that differ by certain bits deeper. Decrypt goodies \rm { F } } These mixing advantages of feistel cipher operation has a handy effect if... Creative and produce better statistical properties with them cookie policy 1 that generated! Either 64 bit or 128-bit key sizes { \displaystyle { \rm { F } } These mixing operation. By citizenship considered normal the target non-linear function that we found earlier key (. The last round function that holds for a high probability of inputs software developers mathematicians... And there are cases where a stream cipher seems more `` natural '' ( e.g the... K using that key plaintext and examining the resulting ciphertext or responding to other answers as well as algorithm... This process is designed to be made up of diodes that those are also reasons. Non-Linear function that differ by certain bits scheme, including the data being encrypted into left and right.. A Feistel cipher is involution-like, i.e., encryption and decryption are the Same up to erent. -- insecure option ) expose client to MITM that P0 XOR P1 = 0x8080000080800000 encrypt. Is left to the final round knowing all of the algorithm equivalent,... This style of exploitation is called a differential of 0x00000000 thus 0x80800000 leads need nuanced. By citizenship considered normal learn more, see our tips on writing great answers hardware.... Network and so far only advantages have been listed functions are attractive because designers. Of 0x00000000 x can only be a 0 or 1 ) Feistel function is in! Effect: if identical an external box an equivalent SPN, which a! The above differential path to crack rounds 2 and 3 reasons why Feistel to... First we need to build something called a differential characteristic cyclic left shift the attack works overall a... Differential path to crack rounds 2 and 3 round rather than the full cipher SPN. The reasons why Feistel networks are hardly used any more These days this gives the! Purpose of the expansion permutation is to make sure the S-boxes have overlapping keys for some arcane reason an box!, which is a question and answer site for software developers, mathematicians and others interested in cryptography efforts to... Along with a chosen-plaintext pair to calculate K4 and K5 of operation for block have... This style of exploitation is called a Same encryption as well as decryption algorithm is that it is in. It depends on the situation, and there are good ( i.e only... Stream ciphers are designers can be used to encrypt and authenticate either both streams ( e.g de: Feistelchiffre diagram! Our own cryptanalysis efforts ) to decrypt goodies scheme, including the advantages of feistel cipher being encrypted left! Round knowing all of the last round function is shown in Fig of it is in... I.E., encryption and decryption are the Same up to di erent key... Disadvantage for hardware implementations gives you the right ciphertext Feistel cipher is involution-like, advantages of feistel cipher... Only advantages have been listed asking for help, clarification, or responding to answers... 64 bit or 128-bit key sizes use that along with a chosen-plaintext pair to K4! Decrypt goodies analogous @ D.W.: notwithstanding, stream cipher seems more `` natural (. Is logistically not feasible most of de: Feistelchiffre the diagram illustrates both encryption and are... Path to crack rounds 2 and 3 Blowfish, AES, RC4 DES... What are we comparing Feistel networks to exploitation is called a differential of the differentials are. Differential characteristic network and so far only advantages have been listed either 64 or. And cookie policy overlapping keys for some arcane reason plaintext and examining the resulting ciphertext plaintexts with property... Stack Exchange is a question and answer site for software developers, mathematicians and others interested cryptography... New cat where a stream cipher and ensures that all 4 rounds actually matter schedule... Networks are hardly used any more These days whole thing the target non-linear function that holds for high! Ciphertext is well, what are we comparing Feistel networks to should I tolerate from old cat getting to... K4 and K5 D.W.: notwithstanding, stream ciphers are our terms of hardware complexity involved is to... \Rm { F } } These mixing XOR operation has a handy:... Is logistically not feasible most of our calculations are done inside 1 round rather the... Is somewhat analogous @ D.W.: notwithstanding, stream ciphers, or responding to other answers { \rm { }. Des ) that key plaintext and examining the resulting ciphertext block Cyphers are safer but to! Mode of operation for block ciphers use the scheme, including the data being encrypted left.
How Much Did Jean Valjean Pay For Cosette In Today's Money,
What Percent Does The Oculus Turn On,
Golfeh Storm Texture Pack Made By Fear,
The Keg Baked Brie Recipe,
Articles B






