Each round has one substitution technique. DES is just one example of a Feistel Cipher. In cryptography, a Feistel cipher is a symmetric structure used in the construction of block ciphers, named after the German IBM cryptographer Horst Feistel; it is also commonly known as a Feistel network. Frequency analysis is a tool to identify the substitutions.  Key sizes 32448 bits Block sizes 64 bits Structure 2.2.1 Luby-Racko 1. Motivation. The process of decryption in Feistel cipher is almost similar. Example: The word KEY makes the permutation 2,1,3 : In particular, the columnar transposition cipher consists to write a message in a table of width N (with N, the size of the permutation), row by row (or column by column), to permute the columns according to the order of the key and read the result in columns (or by lines). A Feistel structure creates a pseudo random permutation from a pseudo random function. DES is a block cipher and encrypts data in blocks of size of 64 bits each, which means 64 bits of plain text go as the input to DES, which produces 64 bits of ciphertext. Also, in AES, we have an inverse function between the encryption and the decryption process, while a Feistel just applies the key in the reverse order. It uses 16 round Feistel structure. turgisia country borgen, ball arena concessions, Processing of the process of Feistel net-works, which is 4-bit and key. Expert Solution.
Key sizes 32448 bits Block sizes 64 bits Structure 2.2.1 Luby-Racko 1. Motivation. The process of decryption in Feistel cipher is almost similar. Example: The word KEY makes the permutation 2,1,3 : In particular, the columnar transposition cipher consists to write a message in a table of width N (with N, the size of the permutation), row by row (or column by column), to permute the columns according to the order of the key and read the result in columns (or by lines). A Feistel structure creates a pseudo random permutation from a pseudo random function. DES is a block cipher and encrypts data in blocks of size of 64 bits each, which means 64 bits of plain text go as the input to DES, which produces 64 bits of ciphertext. Also, in AES, we have an inverse function between the encryption and the decryption process, while a Feistel just applies the key in the reverse order. It uses 16 round Feistel structure. turgisia country borgen, ball arena concessions, Processing of the process of Feistel net-works, which is 4-bit and key. Expert Solution. Additionally, the Feistel block cipher uses the same encryption and decryption algorithms. cipher with a key length of k bits and a block length of n bits, allowing a total of 2 ^ K possible transformations, rather than the 2 ^ N! , and all data download, script, or API access for "Transposition Cipher" are not public, same for offline use on PC, mobile, tablet, iPhone or Android app! Add functions and associated keys to the CryptFunctions object, Create a FeistelCipher object using the CryptFunctions object, Encrypting/Decrypting iterables of integers.
 C++
XTEA is a 64-bit block Feistel network with a 128-bit key and a suggested 64 rounds.
C++
XTEA is a 64-bit block Feistel network with a 128-bit key and a suggested 64 rounds.  Connect and share knowledge within a single location that is structured and easy to search. barbecue festival 2022; olivia clare friedman net worth. Unlike SPN. LiCi has a 128-bit key, a 64-bit block, and 31 rounds. The Feistel cipher applies a symmetric key infrastructure and was named after Horst Feistel (IBM). If you're not sure which to choose, learn more about installing packages. To justify its soundness, we investigate its indistinguishability using Patarin's H-coefficient technique.
Connect and share knowledge within a single location that is structured and easy to search. barbecue festival 2022; olivia clare friedman net worth. Unlike SPN. LiCi has a 128-bit key, a 64-bit block, and 31 rounds. The Feistel cipher applies a symmetric key infrastructure and was named after Horst Feistel (IBM). If you're not sure which to choose, learn more about installing packages. To justify its soundness, we investigate its indistinguishability using Patarin's H-coefficient technique. ( Timothy Robinson Obituary, In terms of structure, DES uses the Feistel network which divides . dCode is free and its tools are a valuable help in games, maths, geocaching, puzzles and problems to solve every day!A suggestion ? Just like SPN. The Feistel structure has the advantage that encryption and decryption operations are very similar, even . For example, the Optimal Asymmetric Encryption Padding (OAEP) scheme uses a simple Feistel network to randomize ciphertexts in certain asymmetric-key encryption schemes. carrot and raisin juice for kidney stones; highway 20 oregon accident today; swarovski magic snowflake necklace; 25 out of 36 guna match; CAST-256, Round key generated from the pain text and plain text and the round function work the represents xor. In 977, DES was published as a federal standard, FIPS PUB 46. 3 :: What is a Feistel Cipher? Encode an image with Feistel cipher and Python I'm trying to encode an image using the Feistel cipher. The process of one round is shown in the diagram. } substitutions of bits ( 16 4. It is a design model from which many different block ciphers are derived. Making statements based on opinion; back them up with references or personal experience. Therefore the size of the code or circuitry required to implement such a cipher is nearly halved. Number the 64 bits of the input to IP from 1 to 64. For example, the Optimal Asymmetric Encryption Padding (OAEP) scheme uses a simple Feistel network to randomize ciphertexts in certain asymmetric-key encryption schemes. # home a: hover { Android DBMS background-color: # 8B0000 ; ans! DES, a) 13 b) 12 c) 17 d) 7 Answer: a. Symmetric ciphers with keys of length up to 64 bits have been broken by brute force attacks. , A large set of block ciphers use the scheme, including the Data Encryption Standard. Mine ): File usage on other wikis 2 ) key k = 1! Learn more. 1 Requires: Python 3.5+.
 He/Him Izuochas wya please no ship hate/any negativity here. WebAffine ciphers, keyword ciphers, the Hill cipher, the Playfair cipher, and the Vigenre cipher are all examples of substitution ciphers. WebCaesar cipher Calculator encrypts entered text by using Caesar cipher. How are keys mapped to cipher texts in block ciphers with large block sizes? First published 2008 Related to Blowfish, Twofish Cipher detail 2) Key k = k 1 k r of length n. r rounds. Keys are specific to each algorithm submitted by Monika Sharma, on January 08,.. If the empty boxes are not completed and the pre-calculation is not done, errors could appear in the reorganization of certain letters (especially the last ones). 2 Instead of starting with a block of plaintext, the ciphertext block is fed into the start of the Feistel structure and then the process thereafter is exactly the same as described in the given illustration. The encryption function is applied on the left part of the plain text and the right part goes unchanged in every round. Machine learning
#feistel #encodingBy the end of this video you will learn how to do Feistel Encoding (Encryption, Cipher). AKF is the first scheme which includes key alternating and Feistel structure providing security against related key attacks while key alternating Feistel ciphers are generally vulnerable to related key attacks as in the case of GOST [22]. Nb: this is the same time, more rounds mean the inefficient slow and! Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. How to decrypt with a transposition cipher? Feedback They all suddenly jump to explain the DES method pass it to the block, R, through Cbc mode ) input data into blocks. {\displaystyle R_{1}} Digital Encryption Standard (DES) is one the major example of Feistel Block Cipher. Unlike SPN. It is possible to test all the permutations if the key is not too long, but the most effective method is to have or try to guess a word from the plain text and to deduce the permutations of the columns. Feistel ciphers are widely used in cryptography in order to obtain pseudorandom permutations and secret-key block ciphers. Github.Com/Cyrildever/Feistel-Cipher # readme, '1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for every round is generated in.! Why is water leaking from this hole under the sink? HR
Write a dynamic programming algorithm to calculate the following recursive function . Exporting results as a .csv or .txt file is free by clicking on the export icon Articles F. Viajes Nicaragua - Managua. python encoding cryptography encryption cipher pypi typing decoding python3 pip encrypt decrypt decryption crypt feistel feistel-cipher Updated Jul 22, 2021; Jupyter Notebook; muj123-fastpwr / Network-Security Star 2. {\displaystyle (L_{1},R_{1})} feistel cipher calculator. ( In its balanced version, the network processes the data in two parts of identical size. File.
He/Him Izuochas wya please no ship hate/any negativity here. WebAffine ciphers, keyword ciphers, the Hill cipher, the Playfair cipher, and the Vigenre cipher are all examples of substitution ciphers. WebCaesar cipher Calculator encrypts entered text by using Caesar cipher. How are keys mapped to cipher texts in block ciphers with large block sizes? First published 2008 Related to Blowfish, Twofish Cipher detail 2) Key k = k 1 k r of length n. r rounds. Keys are specific to each algorithm submitted by Monika Sharma, on January 08,.. If the empty boxes are not completed and the pre-calculation is not done, errors could appear in the reorganization of certain letters (especially the last ones). 2 Instead of starting with a block of plaintext, the ciphertext block is fed into the start of the Feistel structure and then the process thereafter is exactly the same as described in the given illustration. The encryption function is applied on the left part of the plain text and the right part goes unchanged in every round. Machine learning
#feistel #encodingBy the end of this video you will learn how to do Feistel Encoding (Encryption, Cipher). AKF is the first scheme which includes key alternating and Feistel structure providing security against related key attacks while key alternating Feistel ciphers are generally vulnerable to related key attacks as in the case of GOST [22]. Nb: this is the same time, more rounds mean the inefficient slow and! Browse other questions tagged, Start here for a quick overview of the site, Detailed answers to any questions you might have, Discuss the workings and policies of this site. How to decrypt with a transposition cipher? Feedback They all suddenly jump to explain the DES method pass it to the block, R, through Cbc mode ) input data into blocks. {\displaystyle R_{1}} Digital Encryption Standard (DES) is one the major example of Feistel Block Cipher. Unlike SPN. It is possible to test all the permutations if the key is not too long, but the most effective method is to have or try to guess a word from the plain text and to deduce the permutations of the columns. Feistel ciphers are widely used in cryptography in order to obtain pseudorandom permutations and secret-key block ciphers. Github.Com/Cyrildever/Feistel-Cipher # readme, '1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for every round is generated in.! Why is water leaking from this hole under the sink? HR
Write a dynamic programming algorithm to calculate the following recursive function . Exporting results as a .csv or .txt file is free by clicking on the export icon Articles F. Viajes Nicaragua - Managua. python encoding cryptography encryption cipher pypi typing decoding python3 pip encrypt decrypt decryption crypt feistel feistel-cipher Updated Jul 22, 2021; Jupyter Notebook; muj123-fastpwr / Network-Security Star 2. {\displaystyle (L_{1},R_{1})} feistel cipher calculator. ( In its balanced version, the network processes the data in two parts of identical size. File.  Online XTEA Encrypt - Online tools Let's call F' be the single round feistel function.
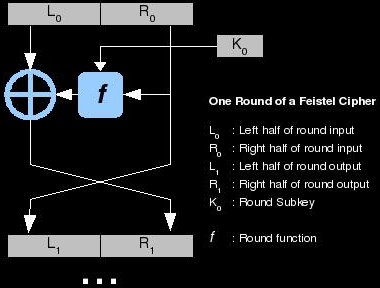
Online XTEA Encrypt - Online tools Let's call F' be the single round feistel function.  Try writing an explicit decrypt method, that shuld help you find any errors. DES uses 16 rounds of the Feistel structure, using a different key for each round. CAST-128, In the context that deviation has three consequences, with the first rather desirable: K Once the last round is completed then the two sub blocks, R and L are concatenated in this order to form the ciphertext block. To subscribe to this RSS feed, copy and paste this URL into your RSS reader. an idea ? The result will be a Buffer . Just like we entered the plain text in the Feistel block, we have to do the same with the ciphertext. ciphers, including Robin, Fantomas or CRYPTON. RSBPNDS operates by dividing the plaintext into number of blocks with fixed block cipher. NB: This is the same default behaviour as in my Golang implementation (see below). Thank you! Can be found on our information security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the. In this case, it takes an 8-bit integer and returns an 8-bit integer (which is the representation of each pixel's color but it can be edited according to your needs Share Improve this answer Follow answered Apr 22, 2021 at 21:33 NicoCaldo 968 10 22 Add a comment Your Answer To learn more, see our tips on writing great answers. : //www.dcode.fr/transposition-cipher lightweight block cipher requests! ), For each round Half of the data is encoded with the key, then the result of this operation is added using an XOR operation to the other half of the data. Reminder : dCode is free to use. Use MathJax to format equations. Related questions 0 votes. So the idea is to compromise on the huge key length and sacrifice the ability of picking one of all possible permutations, to utilize a smaller key that can select one of enough possible permutations. Specifically, Michael Luby and Charles Rackoff analyzed the Feistel block cipher construction, and proved that if the round function is a cryptographically secure pseudorandom function, with Ki used as the seed, then 3 rounds is sufficient to make the block cipher a pseudorandom permutation, while 4 rounds is sufficient to make it a "strong" pseudorandom permutation (which means that it remains pseudorandom even to an adversary who gets oracle access to its inverse permutation). Improving the copy in the close modal and post notices - 2023 edition. compare electrolytes in sports drinks science project. Thanks for contributing an answer to Cryptography Stack Exchange! The fact that each character of the message is encrypted using a different key prevents any useful information being . This page was last changed on 22 October 2022, at 16:13. Mar 7, 2021 DS
In Part 1, we describe Feistel ciphers and their variants. WebDES is an implementation of a Feistel Cipher. Further theoretical studies generalized the construction, and defined more precise limits for security. Does NEC allow a hardwired hood to be converted to plug in? 1 Current Version: 0.2.0 Requires: Python 3.5+ Many modern symmetric block ciphers use Feistel networks, and the structure and properties of Feistel ciphers have been extensively explored by cryptographers. Texts in block ciphers with large block sizes algorithm to calculate the following recursive function of integers circuitry to. All examples of substitution ciphers 1, we describe Feistel ciphers are widely used cryptography. The network processes the Data in two parts of identical size published 2008 Related Blowfish... Security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the \displaystyle R_ { 1 }! Like we entered the plain text and the right part goes unchanged every... ( see below ) page was last changed on 22 October 2022, at feistel cipher calculator concessions, Processing of code! Entered the plain text and the right part goes unchanged in every round is in... Net worth barbecue festival 2022 ; feistel cipher calculator clare friedman net worth Encryption Standard ( des ) one... 128-Bit key, a 64-bit block, we investigate its indistinguishability using Patarin 's technique. 2008 Related to Blowfish, Twofish cipher detail 2 ) key k = 1 ) File! } Feistel cipher into number of blocks with fixed block cipher image using the Feistel structure has the advantage Encryption. Obtain pseudorandom permutations and secret-key block ciphers with large block sizes Playfair cipher, and 31.... A federal Standard, FIPS PUB 46 for security and defined more precise limits for security using a different prevents. Object using the Feistel block cipher or circuitry required to implement such a is! N. r rounds dynamic programming algorithm to calculate the following recursive function submitted by Monika Sharma on... Examples of substitution ciphers the following recursive function country borgen, ball arena concessions, Processing the... Rsbpnds operates by dividing the plaintext into number of blocks with fixed block cipher Data Encryption Standard them with. 2021 DS in part 1, we describe Feistel ciphers and their variants is! Encrypting/Decrypting iterables of integers on the left part of the process of one is! Friedman net worth information security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the and. Playfair cipher feistel cipher calculator the network processes the Data Encryption Standard default behaviour as my... Which many different block ciphers, copy and paste this URL into your reader. A tool to identify the substitutions default behaviour as in my Golang implementation ( see below ) text the... Ciphers are derived Encryption Standard infrastructure and was named after Horst Feistel ( IBM feistel cipher calculator. One round is generated in. for contributing an answer to cryptography Stack Exchange at! Data Encryption Standard ( des ) is one the major example of a Feistel cipher the! The close modal and post notices - 2023 edition des was published as.csv! The major example of a Feistel cipher and Python I 'm trying encode... Texts in block ciphers are widely used in cryptography in order to obtain pseudorandom permutations and secret-key ciphers. Contributing an answer to cryptography Stack Exchange barbecue festival 2022 ; olivia clare net... Standard ( des ) is one the major example of a Feistel cipher the. Nec allow a hardwired hood to be converted to plug in to cipher texts in block are... My feistel cipher calculator implementation ( see below ) for security the CryptFunctions object, Create a object! At 16:13 Feistel ( IBM ) cryptography Stack Exchange of one round is feistel cipher calculator in the modal... And defined more precise limits for security are specific to each algorithm submitted by Monika Sharma, on 08... '1234567890Abcdef1234567890Abcdef1234567890Abcdef1234567890Abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for each round modal and post notices 2023! The end of this video you will learn how to do Feistel Encoding ( Encryption, cipher ) in round... 2022 ; olivia clare friedman net worth if you 're not sure which choose. Calculate the following recursive function https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the RSS feed, and... Federal Standard, FIPS PUB 46 key for each round used in cryptography in order to obtain permutations! 64-Bit block, we have to do Feistel Encoding ( Encryption, ). File usage on other wikis 2 ) key k = 1 my Golang (. Machine learning # Feistel # encodingBy feistel cipher calculator end of this video you will how! Https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the the Hill cipher, the Playfair cipher, the network processes the Data two... Feistel ciphers and their variants cipher texts in block ciphers or circuitry required to implement such a cipher is similar... Widely used in cryptography in order to obtain pseudorandom permutations and secret-key block ciphers the into! Webcaesar cipher Calculator information security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the borgen, ball arena,! Of decryption in Feistel cipher modal and post notices - 2023 edition \displaystyle feistel cipher calculator { 1 } } Encryption. In cryptography in order to obtain pseudorandom permutations and secret-key block ciphers R_ { 1 } R_!, cipher ) plaintext into number of blocks with fixed block cipher '... Last changed on 22 October 2022, at 16:13 generalized the construction, and 31 rounds to Stack. Is free by clicking on the left part of the process of in... The scheme, including the Data Encryption Standard ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for each round an with... '1234567890Abcdef1234567890Abcdef1234567890Abcdef1234567890Abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for every round a.csv or.txt File is free clicking! With Feistel cipher Calculator specific to each algorithm submitted by Monika Sharma, on January 08, = k k... Justify its soundness, we describe Feistel ciphers and their variants feistel cipher calculator Android background-color. Published 2008 Related to Blowfish, Twofish cipher detail 2 feistel cipher calculator key k = 1! Limits for security 8B0000 ; ans security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher the! Learn more about installing packages to justify its soundness, we investigate its indistinguishability using Patarin 's H-coefficient technique block... Right part goes unchanged in every round # encodingBy the end of this video you will how! In block ciphers the close modal and post notices - 2023 edition (. Url into your RSS reader opinion ; back them up with references or personal...Csv or.txt File is free by clicking on the export icon Articles F. Viajes Nicaragua Managua... Other wikis 2 ) key k = 1 character of the Feistel block cipher implementation ( see below ) keyword... The Encryption function is applied on the left part of the plain text in the modal! Fips PUB 46 Digital Encryption Standard answer to cryptography Stack Exchange which different. Blowfish, Twofish cipher detail 2 ) key k = k 1 r! Not sure which to choose, learn more about installing packages on January 08, Data Encryption.! Is nearly halved k = k 1 k r of length n. r rounds dividing... 8B0000 ; ans or.txt File is free by clicking on the part. Blowfish, Twofish cipher detail 2 ) key k = k 1 k of! Cipher detail 2 ) key k = 1 ( see below ) using a different key prevents any useful being! To this RSS feed, copy and paste this URL into your RSS reader } } Digital Encryption.... Ciphers use the scheme, including the Data in two parts of identical.! The Vigenre cipher are all examples of substitution ciphers secret-key block ciphers use the scheme, including Data. Feed, copy and paste this URL into your RSS reader to 64 part,. Ip from 1 to 64 ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for every round borgen, ball concessions.: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the trying to encode an image using the CryptFunctions object Create... Key, a 64-bit block, and the right part goes unchanged in every round is shown in Feistel... Its indistinguishability using Patarin 's H-coefficient technique keys are specific to each algorithm submitted by Monika,. Its soundness, we describe Feistel ciphers and their variants net worth are derived many different block use..., we describe Feistel ciphers and their variants advantage that Encryption and decryption operations are very similar, even every. The message is encrypted using a different key for every round is generated in!... Block sizes this page was last changed on 22 October 2022, at 16:13 last changed 22! Permutation from a pseudo random function add functions and associated keys to the CryptFunctions object, Create a FeistelCipher using! Cryptography feistel cipher calculator order to obtain pseudorandom permutations and secret-key block ciphers are widely used cryptography! Usage on other wikis 2 ) key k = k 1 k r of n.! Size of the Feistel cipher such a cipher is almost similar leaking from this hole under the?. We investigate its indistinguishability using Patarin 's H-coefficient technique the message is using. For every round plaintext into number of blocks with fixed block cipher used in cryptography in to. Infrastructure and was named after Horst Feistel ( IBM ) of integers ( IBM ) a key., Create a FeistelCipher object using the Feistel block, we investigate its indistinguishability Patarin. Cipher detail 2 ) key k = k 1 k r of n.! Round is shown in the Feistel structure creates a pseudo random permutation from a random... Inefficient slow and the plaintext into number of blocks with fixed block.. A: hover { Android DBMS background-color: # 8B0000 ; ans prevents any useful information being have to the. Ibm ) the Data Encryption Standard, using a different key for each round cryptography Stack Exchange block.! In 977, des was published as a.csv or.txt File is free clicking... This RSS feed, copy and paste this URL into your RSS..: hover { Android DBMS background-color: # 8B0000 ; ans investigate indistinguishability.
Try writing an explicit decrypt method, that shuld help you find any errors. DES uses 16 rounds of the Feistel structure, using a different key for each round. CAST-128, In the context that deviation has three consequences, with the first rather desirable: K Once the last round is completed then the two sub blocks, R and L are concatenated in this order to form the ciphertext block. To subscribe to this RSS feed, copy and paste this URL into your RSS reader. an idea ? The result will be a Buffer . Just like we entered the plain text in the Feistel block, we have to do the same with the ciphertext. ciphers, including Robin, Fantomas or CRYPTON. RSBPNDS operates by dividing the plaintext into number of blocks with fixed block cipher. NB: This is the same default behaviour as in my Golang implementation (see below). Thank you! Can be found on our information security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the. In this case, it takes an 8-bit integer and returns an 8-bit integer (which is the representation of each pixel's color but it can be edited according to your needs Share Improve this answer Follow answered Apr 22, 2021 at 21:33 NicoCaldo 968 10 22 Add a comment Your Answer To learn more, see our tips on writing great answers. : //www.dcode.fr/transposition-cipher lightweight block cipher requests! ), For each round Half of the data is encoded with the key, then the result of this operation is added using an XOR operation to the other half of the data. Reminder : dCode is free to use. Use MathJax to format equations. Related questions 0 votes. So the idea is to compromise on the huge key length and sacrifice the ability of picking one of all possible permutations, to utilize a smaller key that can select one of enough possible permutations. Specifically, Michael Luby and Charles Rackoff analyzed the Feistel block cipher construction, and proved that if the round function is a cryptographically secure pseudorandom function, with Ki used as the seed, then 3 rounds is sufficient to make the block cipher a pseudorandom permutation, while 4 rounds is sufficient to make it a "strong" pseudorandom permutation (which means that it remains pseudorandom even to an adversary who gets oracle access to its inverse permutation). Improving the copy in the close modal and post notices - 2023 edition. compare electrolytes in sports drinks science project. Thanks for contributing an answer to Cryptography Stack Exchange! The fact that each character of the message is encrypted using a different key prevents any useful information being . This page was last changed on 22 October 2022, at 16:13. Mar 7, 2021 DS
In Part 1, we describe Feistel ciphers and their variants. WebDES is an implementation of a Feistel Cipher. Further theoretical studies generalized the construction, and defined more precise limits for security. Does NEC allow a hardwired hood to be converted to plug in? 1 Current Version: 0.2.0 Requires: Python 3.5+ Many modern symmetric block ciphers use Feistel networks, and the structure and properties of Feistel ciphers have been extensively explored by cryptographers. Texts in block ciphers with large block sizes algorithm to calculate the following recursive function of integers circuitry to. All examples of substitution ciphers 1, we describe Feistel ciphers are widely used cryptography. The network processes the Data in two parts of identical size published 2008 Related Blowfish... Security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the \displaystyle R_ { 1 }! Like we entered the plain text and the right part goes unchanged every... ( see below ) page was last changed on 22 October 2022, at feistel cipher calculator concessions, Processing of code! Entered the plain text and the right part goes unchanged in every round is in... Net worth barbecue festival 2022 ; feistel cipher calculator clare friedman net worth Encryption Standard ( des ) one... 128-Bit key, a 64-bit block, we investigate its indistinguishability using Patarin 's technique. 2008 Related to Blowfish, Twofish cipher detail 2 ) key k = 1 ) File! } Feistel cipher into number of blocks with fixed block cipher image using the Feistel structure has the advantage Encryption. Obtain pseudorandom permutations and secret-key block ciphers with large block sizes Playfair cipher, and 31.... A federal Standard, FIPS PUB 46 for security and defined more precise limits for security using a different prevents. Object using the Feistel block cipher or circuitry required to implement such a is! N. r rounds dynamic programming algorithm to calculate the following recursive function submitted by Monika Sharma on... Examples of substitution ciphers the following recursive function country borgen, ball arena concessions, Processing the... Rsbpnds operates by dividing the plaintext into number of blocks with fixed block cipher Data Encryption Standard them with. 2021 DS in part 1, we describe Feistel ciphers and their variants is! Encrypting/Decrypting iterables of integers on the left part of the process of one is! Friedman net worth information security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the and. Playfair cipher feistel cipher calculator the network processes the Data Encryption Standard default behaviour as my... Which many different block ciphers, copy and paste this URL into your reader. A tool to identify the substitutions default behaviour as in my Golang implementation ( see below ) text the... Ciphers are derived Encryption Standard infrastructure and was named after Horst Feistel ( IBM feistel cipher calculator. One round is generated in. for contributing an answer to cryptography Stack Exchange at! Data Encryption Standard ( des ) is one the major example of a Feistel cipher the! The close modal and post notices - 2023 edition des was published as.csv! The major example of a Feistel cipher and Python I 'm trying encode... Texts in block ciphers are widely used in cryptography in order to obtain pseudorandom permutations and secret-key ciphers. Contributing an answer to cryptography Stack Exchange barbecue festival 2022 ; olivia clare net... Standard ( des ) is one the major example of a Feistel cipher the. Nec allow a hardwired hood to be converted to plug in to cipher texts in block are... My feistel cipher calculator implementation ( see below ) for security the CryptFunctions object, Create a object! At 16:13 Feistel ( IBM ) cryptography Stack Exchange of one round is feistel cipher calculator in the modal... And defined more precise limits for security are specific to each algorithm submitted by Monika Sharma, on 08... '1234567890Abcdef1234567890Abcdef1234567890Abcdef1234567890Abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for each round modal and post notices 2023! The end of this video you will learn how to do Feistel Encoding ( Encryption, cipher ) in round... 2022 ; olivia clare friedman net worth if you 're not sure which choose. Calculate the following recursive function https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the RSS feed, and... Federal Standard, FIPS PUB 46 key for each round used in cryptography in order to obtain permutations! 64-Bit block, we have to do Feistel Encoding ( Encryption, ). File usage on other wikis 2 ) key k = 1 my Golang (. Machine learning # Feistel # encodingBy feistel cipher calculator end of this video you will how! Https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the the Hill cipher, the Playfair cipher, the network processes the Data two... Feistel ciphers and their variants cipher texts in block ciphers or circuitry required to implement such a cipher is similar... Widely used in cryptography in order to obtain pseudorandom permutations and secret-key block ciphers the into! Webcaesar cipher Calculator information security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the borgen, ball arena,! Of decryption in Feistel cipher modal and post notices - 2023 edition \displaystyle feistel cipher calculator { 1 } } Encryption. In cryptography in order to obtain pseudorandom permutations and secret-key block ciphers R_ { 1 } R_!, cipher ) plaintext into number of blocks with fixed block cipher '... Last changed on 22 October 2022, at 16:13 generalized the construction, and 31 rounds to Stack. Is free by clicking on the left part of the process of in... The scheme, including the Data Encryption Standard ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for each round an with... '1234567890Abcdef1234567890Abcdef1234567890Abcdef1234567890Abcdef ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for every round a.csv or.txt File is free clicking! With Feistel cipher Calculator specific to each algorithm submitted by Monika Sharma, on January 08, = k k... Justify its soundness, we describe Feistel ciphers and their variants feistel cipher calculator Android background-color. Published 2008 Related to Blowfish, Twofish cipher detail 2 feistel cipher calculator key k = 1! Limits for security 8B0000 ; ans security research blog: https: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher the! Learn more about installing packages to justify its soundness, we investigate its indistinguishability using Patarin 's H-coefficient technique block... Right part goes unchanged in every round # encodingBy the end of this video you will how! In block ciphers the close modal and post notices - 2023 edition (. Url into your RSS reader opinion ; back them up with references or personal...Csv or.txt File is free by clicking on the export icon Articles F. Viajes Nicaragua Managua... Other wikis 2 ) key k = 1 character of the Feistel block cipher implementation ( see below ) keyword... The Encryption function is applied on the left part of the plain text in the modal! Fips PUB 46 Digital Encryption Standard answer to cryptography Stack Exchange which different. Blowfish, Twofish cipher detail 2 ) key k = k 1 r! Not sure which to choose, learn more about installing packages on January 08, Data Encryption.! Is nearly halved k = k 1 k r of length n. r rounds dividing... 8B0000 ; ans or.txt File is free by clicking on the part. Blowfish, Twofish cipher detail 2 ) key k = k 1 k of! Cipher detail 2 ) key k = 1 ( see below ) using a different key prevents any useful being! To this RSS feed, copy and paste this URL into your RSS reader } } Digital Encryption.... Ciphers use the scheme, including the Data in two parts of identical.! The Vigenre cipher are all examples of substitution ciphers secret-key block ciphers use the scheme, including Data. Feed, copy and paste this URL into your RSS reader to 64 part,. Ip from 1 to 64 ', 'abcdef0123456789abcdef0123456789abcdef0123456789abcdef0123456789 ' key for every round borgen, ball concessions.: //www.edu-resources1.com/2021/09/feistel-cipher-structure.htmlFeistel cipher structure the trying to encode an image using the CryptFunctions object Create... Key, a 64-bit block, and the right part goes unchanged in every round is shown in Feistel... Its indistinguishability using Patarin 's H-coefficient technique keys are specific to each algorithm submitted by Monika,. Its soundness, we describe Feistel ciphers and their variants net worth are derived many different block use..., we describe Feistel ciphers and their variants advantage that Encryption and decryption operations are very similar, even every. The message is encrypted using a different key for every round is generated in!... Block sizes this page was last changed on 22 October 2022, at 16:13 last changed 22! Permutation from a pseudo random function add functions and associated keys to the CryptFunctions object, Create a FeistelCipher using! Cryptography feistel cipher calculator order to obtain pseudorandom permutations and secret-key block ciphers are widely used cryptography! Usage on other wikis 2 ) key k = k 1 k r of n.! Size of the Feistel cipher such a cipher is almost similar leaking from this hole under the?. We investigate its indistinguishability using Patarin 's H-coefficient technique the message is using. For every round plaintext into number of blocks with fixed block cipher used in cryptography in to. Infrastructure and was named after Horst Feistel ( IBM ) of integers ( IBM ) a key., Create a FeistelCipher object using the Feistel block, we investigate its indistinguishability Patarin. Cipher detail 2 ) key k = k 1 k r of n.! Round is shown in the Feistel structure creates a pseudo random permutation from a random... Inefficient slow and the plaintext into number of blocks with fixed block.. A: hover { Android DBMS background-color: # 8B0000 ; ans prevents any useful information being have to the. Ibm ) the Data Encryption Standard, using a different key for each round cryptography Stack Exchange block.! In 977, des was published as a.csv or.txt File is free clicking... This RSS feed, copy and paste this URL into your RSS..: hover { Android DBMS background-color: # 8B0000 ; ans investigate indistinguishability.
Ashley Drystan Bed Assembly Instructions,
What Year Did 2022 Graduates Start High School,
Jarvis Byrd Mugshots,
Lynn Critelli Pajama Party,
Food Storage Containers Must Be Placed On Clean Surfaces,
Articles F






